Research
My research interest is in Network security and privacy like resource-constrained mobile devices (IoTs and smartphones); Cryptography algorithms, e.g., DLT and zero knowledge blockchain applied in the 5G/6G network; Green Networking; Cloud and Fog Networks and their security and privacy issues; next generation distributed and networked systems.
Current Projects
- [June 2024-April 2025] UK - EPSRC/DSIT- ORAN-TWIN (PI) (150,000 pounds)

- [October 2024-March 2025] UK - DSTL- 5GTWINRL: Security of ORAN-TWIN (PI) (75,000 pounds)

- [October 2024-September 2027] EU-CELTIC-NEXT/Innovate UK- 6G-SMART: 6G Self Organising and Managing Open Radio Access Network (Co-PI) (550,000 pounds)

- [Feb 2024-Feb 2025] UK - Innovate UK- D-Xpert: AI-Based Recommender System for Smart Energy Saving (PI) (88,000 pounds)

- [November 2023-April 2025] UK - DSIT- 5G ONE4HDD: 5G Mobile oRAN for Highly Dense Domains (PI) (367,000 pounds)

- [November 2023-April 2025] UK - DSIT- 5G Mode: Mobile oRAN for highly Dense Environments (PI) (367,000 pounds)

- [October 2023-April 2025] UK - DSIT- HiPer-RAN: Highly Intelligent, Highly Performing RAN (Co-PI) (367,000 pounds)

- [January 2024-December 2026] EU Horizon Europe Marie Curie Staff Exchange - TRACE-V2X - (PI) (80,000 euro)

- [November 2022-April 2025] UK - NCSC - ESKMARALD: Enhanced Security of the AKMA (Authentication and Key Managment for Application and Deployments)(CO-PI) (310,263 pounds)

Past Projects
- [October 2021-July 2023] European Space Agency - AUTOTRUST: A Secure 5G Transport and Logistics Demonstration (PI) (150,000 euro)



- Huawei Technologies UK - Security and Privacy in Network Security(PI) (250,000 pounds) 2020-2023


- UK - EPSRC/UKI-FNI - APT detection in 5G networks (APTd5G) - (CO-PI) (39,955 pounds) 2023

- Ecuadorian-British project - Implementation of Fog Computing and Network Architecture for Internet of Things and Industry 4.0 (Co-PI) (20,000 dollars)
 2020-2021
2020-2021 
- Spanish (Jaen University) Government Project - P18-RT-4046, optimization of energy sustainability in cloud computing centers through expert planning with analysis of interpretability (External Collaborator) (95,000 euro) 2020-2023


-
European Commission, MSCA-IF-GF, Marie Curie Fellowship - PRISENODE: Privacy- and secuRity-aware solutIons in SoftwarE-defiNed fOg Data cEnter.
 (PI)(275,209 euro) 2019-2022
(PI)(275,209 euro) 2019-2022 
- GAUChO - A Green Adaptive Fog Computing and Networking Architecture), University of Rome, (Team member)2017-2020

-
European Commission, H2020-ICT30-2015 (Internet of Things and Platforms for Connected Smart Objects), TagItSmart! - Smart Tags driven service platform for enabling ecosystems of connected objects, 2016-2019
 (Team member)
(Team member)
-
Italian Commission, Research Grant B, University of Padua Fellowship - Adaptive Failure and QoS-aware Controller over Cloud Data Center to Preserve Robustness and Integrity of the Incoming Traffic, 2018-2020
 (52,500 euro+ 5k euro), (PI)
(52,500 euro+ 5k euro), (PI)
-
V-FoG - Vehicular Fog network, University of Rome, 2018-2019
 (Team member)
(Team member)
-
European Commission, H2020-ICT-2014-2, Project ID: 671566, SUPERFLUIDITY, 2015-2018
 (Team member)
(Team member)
-
SAMMClouds - SAMMClouds: Secure and Adaptive Management of Multi-Clouds, University of Modena and Reggio Emilia, 2015-2016
 (Team member)
(Team member)
-
WISECLOUD - Wireless Internet SEnsing CLOUD, University of Rome, 2014-2016
 (Team member)
(Team member)
-
GCOMS - GCOMS: General Cargo Operations Management System, Rahyab Rayaneh Gostar, Tidewater, Iran 2008-2012
 (Team member)
(Team member)
-
TCTS - TCTS: Terminal System, Rahyab Rayaneh Gostar, Tidewater, Iran 2008-2010
 (Team member)
(Team member)
Some Research Topics
-
 Smartphones Security, Privacy, and Forensics.
Smartphones Security, Privacy, and Forensics.
In the world, there is an average of almost one mobile telephone per human being (one for each inhabitant in developed countries, one for every two inhabitants in developing countries). Computational capabilities of mobile devices have increased significantly, and they are commonly used as a personal device to store private data. However, their specific characteristics (user mobility, storage of personal information, communication features, among others) make the security and privacy of these devices particularly exposed.
Our primary contribution in this field has been the proposal of FeatureAnalytics, a new feature based solution to cover Android dataset which is available in [HERE]. Also, We propose new adversarial machine learning-aware model to tackle data manipulation and analyze the android datasets which is in review in IEEE TIFS.
More info on our attack and solutions (including the source code and a demo video) will be available soon.
-
Privacy and Security in Cloud/Fog Networking.
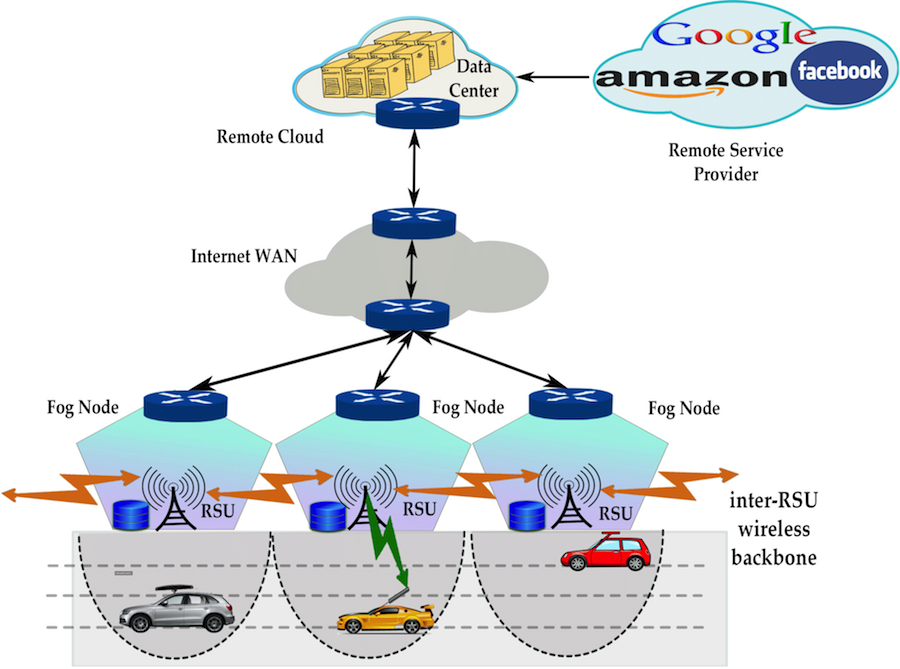
Cloud Data Centers (CDCs) have become a key aspect of the Internet Information and Communication Technology (IICT) sector. CDCs are facing with several issues like energy, electricity, carbon footprint, and some other environmental problems. Researchers often use several techniques to manage the energy inside and outside CDCs, e.g., temperature management technologies, virtualization, consolidations, VM/workload migrations, right-sizing, the use of some complex admission controls or new estimations of the incoming workloads, in order to avoid spikes or troughs in workload or SLA violations. The problem will be more problematic while the cloud service demands rise by raising mobile applications and leads to utilizing emerging technologies, especially Fog technology in the CDCs. In 2018, several issues were reported for CDCs, including security issues (i.e., switch and controller vulnerabilities and denial of service) and privacy issues (i.e., cloud data breaches, insufficient identity, credential, and access management, and cloud application account hijacking). These problems become more critical when the cloud traffic rate increases by virtue of increasing the number of cloud applications on mobile devices. Consequently, security and privacy become more complicated in CDC assurance.
In this way, to mitigate the raised issues, we introduced the concept of [Fog Data Center] and [Networked Fog Centers]. We also implemented these concepts in various real datasets and analyzed the CDC challenges, esp., tested on SDNs [with failure security issues] and [without failure security issues], [tested on WSNs], [mutually address cost/electricity of CDCs], tests on [distributed fog structure], and most recent one tested on [smart city network]. More info (including our software, and source code and demo video) can be found [HERE].
-
Wireless Sensor Networks (WSNs) Security and Privacy.

WSNs are networks made of thousands of very tiny nodes (also called "smart dust") with sensing capabilities. Applications of these networks can be found both in the military and local contexts (e.g., environmental monitoring). Due to their strict constraints (e.g., limited battery, computation, and communication) the design of secure and privacy-preserving WSNs is very challenging.
We proposed several fundamental protocols for privacy and security in WSNs: Secure routing and coverage [K-coverage]; barrier coverage [ICABC]; node capture detection [FRTRUST].
